What Can We Learn From The Spear Phishing Exploits Against Telstra

Cybersecurity researchers have warned the public that there is a convincing phishing email pretending to be coming from Telstra, the Telco giant. The sample provided falls into the category of ‘spear phishing’, which means only those that are current customers of Telstra received it. Using clever formatting tricks, the email looks the same as a genuine Telstra email.
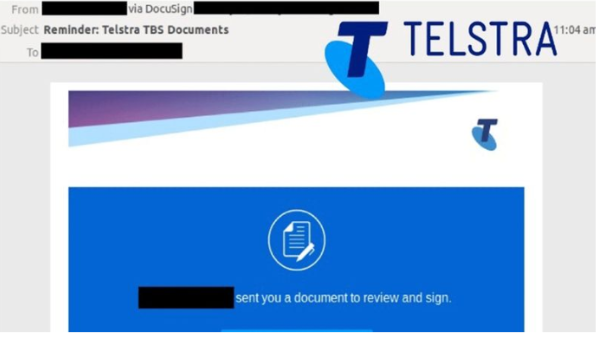
The spear-phishing email contains a malicious file with the goal of stealing information from the user in the background. As reported by MailGuard, a cloud-based email security consulting firm, the phishing email claiming to be coming from ‘Telstra Business Centre’ branch.
“It claims that a user from a Telstra Business Centre branch is the sender of the document, with their name used in multiple locations including the message body. The inclusion of both Telstra and DocuSign logos and branding within the email makes it harder for recipients to identify the email as a scam as it appears as a legitimate notification. In such cases, users are reminded of the importance of not accepting/clicking on documents from unknown senders, despite the organization they purport to be from. All attachments/links should only be accessed when users are certain about the credibility of their owners,” explained MailGuard’s representative.
Telstra on their end reminded their customers to visit https://www.telstra.com.au/help/contact-us/scams, their official website for reporting phishing emails and additional information on how to prevent falling for scams. Telstra also emphasized that their official communication does not contain wrong grammar, URL links to questionable websites and general-sounding email.
To avoid being a victim of this type of cybercrime, we must take into consideration some tips:
- When creating passwords, the ideal is a sequence of a minimum of eight characters that combine letters and numbers and also does not correspond to the proper name of someone close or a word that is easily guessable for a ‘hacker’.
- It is important to periodically change the password used to access Internet services, whether social networks, email or any other. In addition, it is not advisable to use the same word in all passwords, since that way the account will be more vulnerable.
- When receiving a link in the email, it is convenient to look at the exact address of the sender, regardless of the name that appears.
- It is essential in a computer connected to the Network a good equipment ‘software’ to fight against attacks. Among them, it includes a good antivirus and protection against spies that are constantly updated. To these programs, we must add a firewall and an anti-spam filter.
- Do not trust the software that some web pages offer to download. If it seems harmful, it is very likely to be harmful. Also, the attachments in the email are good drivers of malicious software.
- When using a shared computer, it is convenient not to save the password when the browser suggests it.
- Even, it would be necessary that the bank statements were checked carefully in search of some strange operation.