5 Simple Ways to Spy on Someone’s Phone Without Touching It
People often want to find out what their partners or their children or other loved ones are doing in their absence. This would have been impossible some years back, but…
Read More
People often want to find out what their partners or their children or other loved ones are doing in their absence. This would have been impossible some years back, but…
Read More
The United States has accused a Russian defense contractor company named Special Technology Center (STC) for developing specialized software to spy on Android users. For many years, the western nations…
Read More
Are you a Samsung smartphone user? Then this news item is for you; we recommend to only accept official updates for your Samsung Device using the official Kies app or…
Read More
Have you ever seen the warning message on your Google Android smartphone: Android storage is insufficient? This means that you do not have enough space to take more photos or…
Read More
Android e-readers are not taking any headlines when manufacturers are announcing their products. However, the e-ink based Android tablets are still selling like hotcakes, given it provides more flexibility than…
Read More
Last week, NIST announced version 1.0 of its Privacy Framework, a tool designed to support organizations in managing their privacy risks. In September 2019, NIST released a revised draft Privacy…
Read More
GDPR ,or the General Data Prevention Regulation, is a new law that has been enforced by the European Union since May 25, 2018. The goal of this regulation is to…
Read More
In May 2018, the General Data Protection Regulation (GDPR) was enforced by the European Union (EU) to protect its citizens from the misuse of their personal data. This breakthrough regulation…
Read More
Symantec, a mainstream antimalware vendor has disclosed the result of their study that reveals that 67% of hotel websites experienced leaks with its respective booking systems. The leakage continues and…
Read More
Distributed denial-of-service attacks pose an increasing threat to organizations, with even some of the largest firms suffering significant disruptions from such attacks. Attackers use botnets of compromised IoT devices to…
Read More
Telegram Messenger, which had suffered a DDoS (Distributed Denial of Service) attack recently, has reportedly recovered from the same and everything now seems stabilized, as per reports. A ZDNet report,…
Read More
A “denial-of-service condition” has reportedly impacted a US energy company that provides power to many western states. TechCrunch reports, “An energy company providing power in several western U.S. states experienced…
Read More
For any enterprise today, a DDoS (Distributed Denial of Service) attack could mean a real headache. Such an attack could throw out of gear all business activities and all operations…
Read More
The threat of DDoS (Denial-of-Service) attacks that send massive processing demands from multiple Internet-connected devices (be it a PC, a smartphone, a tablet or an IoT) to the target server…
Read More
Meanwhile, here is the best alternative to access the best Torrents sites that is a well-known and widely used and accessed by more than millions of visitors daily across the…
Read More
Cloud Services Infographic It’s worth it, cloud computing includes benefits and gives you the flexibility of connecting to your business from anywhere, any time. Increase operation efficiency and reduce IT…
Read More
IoT success. The companies that succeed in transforming their operations and business models through IoT are those that will have weighed all the considerations, planned thoroughly, and implemented carefully. Related…
Read More
Discussing basic data loss prevention steps. Data loss prevention can be done by doing certain basic things like installing a firewall and anti-virus software, ensuring proper backup of files and…
Read More
Cyber threats can wreak havoc on businesses, from data breaches to loss of reputation. Luckily, there are effective strategies available that can reduce cybersecurity risk. Avoidance is one of the…
Read More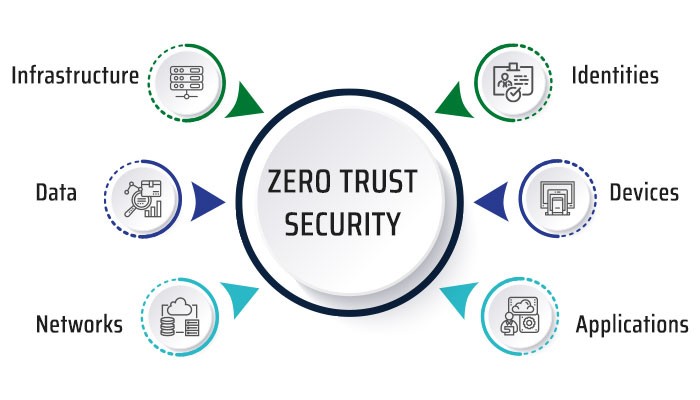
Zero trust security takes an “never trust, always verify” approach to access control. Access is only granted once an individual’s identity and context have been confirmed through multifactor authentication and…
Read More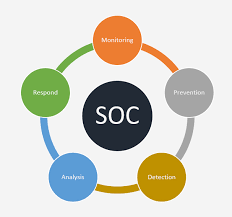
A Security Operations Center (SOC) specializes in monitoring and analyzing data to detect cyber threats and prevent attacks from them. They work to sort actual threats from false positives before…
Read More

The Extended Detection and Response Platform (XDR) ingestion and correlation technology captures and correlates high-fidelity data across your security layers, such as endpoint, network, logs, cloud services and identities to…
Read More
Endpoint detection and response (EDR) tools offer businesses that employ hybrid work models or remote employees an extra layer of cybersecurity protection. Utilizing artificial intelligence (AI) and machine learning (ML),…
Read More
EDR can detect and respond to emerging and advanced cyber threats quickly and efficiently, making it an essential component of modern business ecosystems. Beyond signature-based detection capabilities, its features go…
Read More
Cloud security involves employing perimeter defenses like firewalls, IDPSs and VPNs as well as guaranteeing isolation through network segmentation and virtual LANs while monitoring traffic for anomalies and threats –…
Read More
Antivirus software protects devices against viruses, malware, and other cyberthreats by detecting, quarantining, and deleting malicious code. Modern antivirus products also offer additional security features such as password protection, identity…
Read More
Criminal hackers employ ransomware attacks against their targets by encrypting their data and demanding that a ransom be paid within an allotted timeframe or risk losing it forever. When an…
Read More
Distributed denial-of-service attacks pose an increasing threat to organizations, with even some of the largest firms suffering significant disruptions from such attacks. Attackers use botnets of compromised IoT devices to…
Read More