WannaCry Out, SamSam Ransomware In
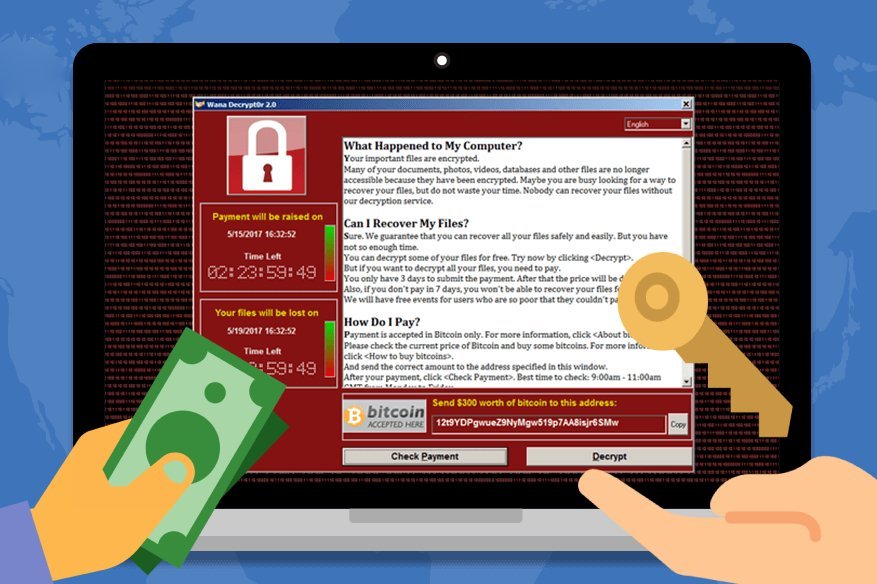
Ransomware has taken the stage of malware infestation by storm, as it is designed not to shy away from victims. On-screen announcements such as the one below promote anger and worry. It is designed to create panic and hopelessness as the encryption of their important data is completed, and can only be reversed with a fee:
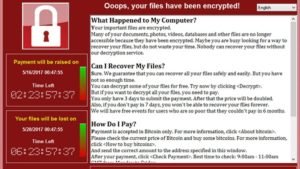
Above is the announcement window once a vulnerable PC is infected by WannaCry, the number 1 malware for 2017. It is scary with the use of a red palette for its window and creates urgency as a ticking timer counts down up to when the user can pay the ransom.
Ransomware in its present form looks like a modern way to extort money from the poor victims that accidentally trigger the malware in one way or another. However, the idea of helding user data hostage, until payment is received is nothing new. The AIDS Trojan of 1989, during the DOS era, was WannaCry’s great-grandparent:
The cybersecurity industry continues to strive to help users fight contemporary ransomware, this is fairly evident with the launch of nomoreransom.org. It is a non-profit initiative where various ransomware variants with known decryptors are posted. It is a partnership of the Netherland’s police, European Cybercrime Center and two mainstream antivirus companies, McAfee and Kaspersky.
However, the cybercriminals have taken the challenge of keeping antimalware from detecting their creations. This is due to their continued persistence with research and development, to find new ways to penetrate vulnerable computers with the least effort as possible.
One of the successful results of their persistence is the newly discovered SamSam ransomware. It does not discriminate when it comes to possible victims, huge businesses, government computers, healthcare industry, and retailers to name a few categories of entities that fell victim to it. Lack of adequate backup solution is the primary motive for certain victims to just pay the ransom, in order to get their precious data back. The cloud-storage backup vendors these days are a dime-a-dozen, and it is still unfortunate that many companies choose not to have a decent backup and restore policy.
Samsam takes advantage of the weakness in the FTP protocol, Java plugin, and Remote Desktop in order to penetrate a computer from the network. This is not the fault of OS developer like Microsoft, as the exploits used usually be already patched months prior. The responsibility falls on the shoulders of system administrators, for not patching the vulnerable machines as some are afraid that patches introduce conflict and incompatibility with user applications.
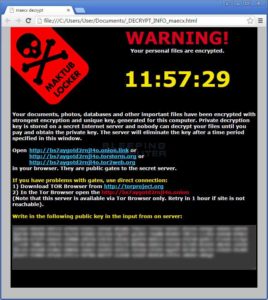
Like WannaCry, Samsam used an announcement window that users can never ignore. Using a scary black palette, the notification window declares the encryption of user data, ordering the victim to pay within a specific time limit only.
Ransomware operates in stages, all of these are automated and the user cannot stop the process once started:
- High-end 2048-bit encryption process
- Private key is held by the attacker, and stored in a command and control server. The CAC server will only release the private key to the victim once payment has been verified.
- Look if a public decryptor is available in nomoreransom.org. If it is available, using the decryptor is the best way to reverse the encryption.
- From the point of being encrypted, the only way to legitimately recover is by reformatting/reimaging the PC and restoring the latest version of the original data from a known good backup. There is no shortcut to it, as paying the ransom promotes further development of more complex and sophisticated malware in the future.
This is why it is important for everyone to be alert with all the files they use with the computer, as it may end up being a trojan, pretending to be a legitimate application, even if it is actually malicious. SamSam, like WannaCry that preceded it, is designed to maximize profit for its authors. It is healthy for everyone to maintain doubt when using random software and clicking random links online.