22 Apps in Google Play Store Taken Down Due To Backdoor Downloaders
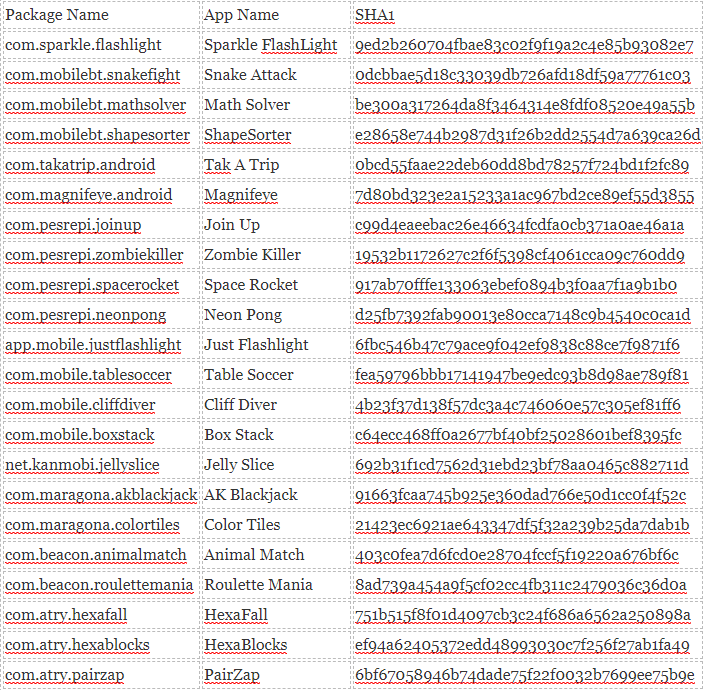
Google continues its quest to keep Android users safe by actively banning apps they think will harm its users. This time around, a batch of 22 apps was deleted by the search giant from the Google Play Store. Unfortunately, the aggregate download of the apps reached more than two million downloads prior to the takedown. The justification for the takedown is the alleged embedded backdoor downloader that is hidden with the following apps:
“Andr/Clickr-ad is a well-organized, persistent malware that has the potential to cause serious harm to end users, as well as the entire Android ecosystem. These apps generate fraudulent requests that cost ad networks significant revenue as a result of the fake clicks. From the user’s perspective, these apps drain their phone’s battery and may cause data overages as the apps are constantly running and communicating with servers in the background. Furthermore, the devices are fully controlled by the C2 server and can potentially install any malicious modules upon the instructions of the server,” explained Sophos.Dubbed ‘Andr/-ad’ malware by Sophos, a mainstream antimalware vendor, the malware integrates itself to Android, as apps mentioned above install themselves to the startup routine of the device. They automatically run in the background, without the user knowing, hence consuming resources on the device like battery life, memory and data connection.
Its virus author registered mobbt.com as the command and control domain, apps connect to that domain to further receive new instructions, download unauthorized adverts and updates the virus itself. The unsuspecting users will not be able to detect the app displaying the adverts, as it is not drawing any pixels on the screen. The click-advert system also a fraudulent business, as the advertisers are fooled in the process, they will be very pleased with the ‘high traffic’ for their adverts, even though the numbers were just manufactured by the apps. The malware has the capability to change user agent on-the-fly. It can identify itself as an Android device and even an iPhone. This creates a unique ‘simulated’ clicks from 249 models of smartphones from 33 vendors. It is still unknown of this point the real people behind the 22 apps, as they seem to be coming from similar authors. With a wide diversity of the phone being simulated, advertisers are attracted to sign-up for the advertising campaign pushed by the virus author.