Global Threat Statistics for the week of March 22, 2019

PayPal Phishing Casts a Wide Net
One of the most successful phishing methods is to co-opt a well-respected brand. PayPal topped the list by a wide margin in a recent analysis of over 100 million endpoints by Comodo Threat Intelligence Lab. PayPal was impersonated in 39% of all such attacks, with Microsoft a distant second at 20%.
Sharing this information is important so that your users know to be more vigilant if they get an email or alert, supposedly from PayPal, Microsoft, or the others in this chart. Some of these phishing websites look quite authentic and may fool even security-minded users. This type of information is a great addition to your security awareness program.
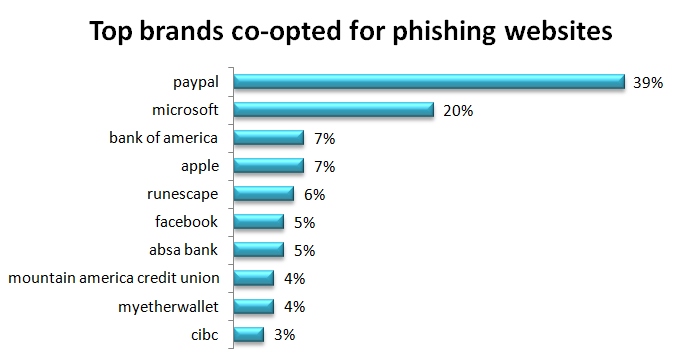
The scale at which these attacks are being deployed is evident in the number of web pages using this type of attack. This analysis discovered 61,767 web pages impersonating these brands for the purpose of phishing. Just over half were taken down by the time this article was written. That still leaves almost 30,000 malicious web pages to lure your users.
6 characteristics that make brands good targets for phishing impersonation
1. Registered user accounts
Brands that have hundreds of thousands of registered user accounts are an inviting target for cybercriminals. Consider, for example, PayPal with 267 million registered user accounts. If an attacker can send phishing emails to 1% of them, that’s 2.67 million chances that a user will click on a link that brings that user to their malicious website. If just 1% of those users click that link, they get 26,700 accounts that they have compromised.
2. Trusted brand
When dealing with a trusted brand, people tend to let their guard down. If a phishing website impersonates a trusted brand well enough, that lower level of user vigilance increases the chances of a successful attack.
3. Access to money
In most cases, this is the ultimate goal. There are other motivations such as hacktivism or cyber warfare.
4. Access to information
Information is often used as a means to financial gain, either by selling the information or by using it to access bank accounts or other financial resources.
5. Emotional triggers
Phishing taps into our emotions to get us to click that link. Fear is commonly used, such as claims that you will lose money or your data. Emotions can override logical thinking and make people take careless actions.
6. Ease of use and availability of attack tools
Cybercriminals like to share information and tools that make it easy for others to launch attacks. It stands to reason that the easier it is to launch an attack, to more likely someone is to do so.
More Than Half of Phishing Impersonations Used PayPal or Microsoft
It is this last characteristic that most likely draws cybercriminals to PayPal more than others, accounting for 39% of brand impersonations. Attack tools are readily available and easy to use. A Google search for “PayPal phish” brings up “paypal phishing tutorial” as the sixth search prediction. Google search predictions are based on what other people have already searched for. That tells us that a lot of people have searched for “paypal phishing tutorial,” and they have found plenty of tutorials explaining how to set up a phishing web page that impersonates PayPal. Of course, more detailed tutorials with scripts for capturing user information are also available on the dark web.
Aside from the ease of phishing under the pretext of being PayPal, the 267 million PayPal users are a huge target. People rely on PayPal to make and receive payments, so an email that those payments may fail triggers a response, eager to correct the problem. In that desire to fix the problem, people can miss subtle signs that this may not be legitimate.
Once they get you on the hook, they see how far they can reel you in. They start by prompting you for PayPal login credentials using an authentic-looking PayPal login prompt. That gives them access to your PayPal funds and whatever access you’ve granted PayPal to linked bank accounts. Then they ask for verification which can include any or all of your birth date, social security number, and bank account numbers. Depending on how much you provide, they may have all they need for identity theft. As if that’s not bad enough, malware may be downloaded along the way so they also have access to your laptop or whatever device you are using. If it’s a device you use on a corporate network, they now also have a path into whatever corporate resources you have access to.
Access to your laptop/device is the goal of the second most co-opted brand for phishing, Microsoft, who have said they have about 700 million active Windows 10 users. The phishing usually comes in the form of a pretext of Microsoft technical support claiming they will fix some horrible (but somehow symptomless) problem you have. The goal is to have the user give them remote access to “fix” the laptop. Once the access is granted, they install malware that will typically include a keystroke logger and other tools to send them useful information from the device.
Users on corporate devices will usually not fall for that since they expect the IT department to handle that. However, if you allow your users to VPN in from home, a compromised device on the home network may then pass malware to the corporate device or access the corporate network through the VPN.
Countries and Regions Hosting Malware and Botnets
There are a number of variables that impact where malware and botnets may be hosted, such as availability of target computers, ease of access, the vulnerability of accessible computers, type of malware. These are constantly changing, so it introduces a bit of randomness to the results, making the statistics that follow a snapshot in time.
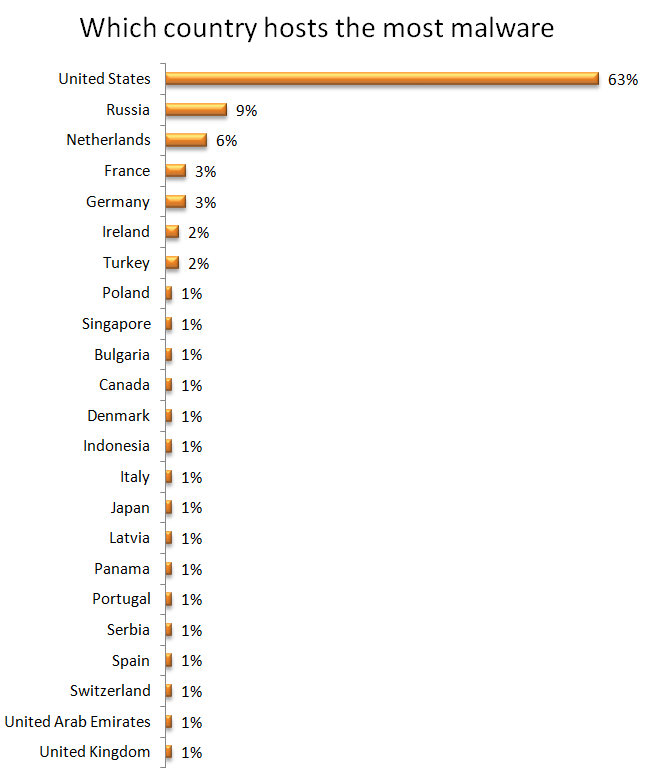
The United States, at 63%, hosted seven times as much malware as the next highest, Russia at 9%. Netherlands, France, Germany, Ireland, and Turkey follow, with all other countries listed hosting only 1% each.
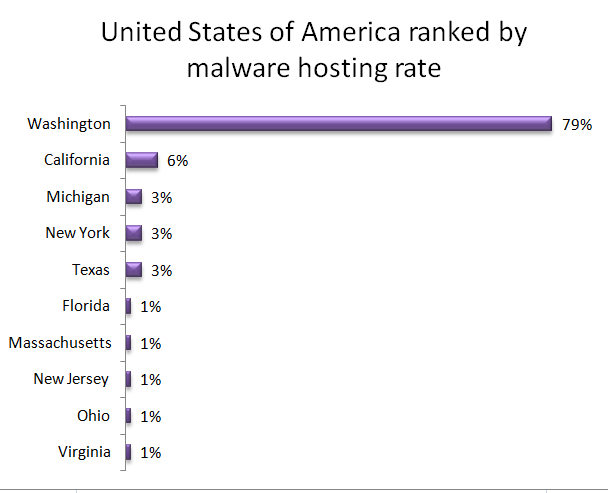
Within the United States, an astonishing 79% of malware was hosted in the state of Washington. California followed with 6%. Michigan, New York, and Texas each hosted 3% with the remaining listed states each at 1%.
The strategy for finding hosts is different for a botnet than it is for malware. Botnets are typically built to have as many hosts as possible participating in the botnet. While many of the variables discussed for malware are the same, the strategy around quantity yields very different results. The United States hosted only 4% of botnets, compared with 63% of malware.
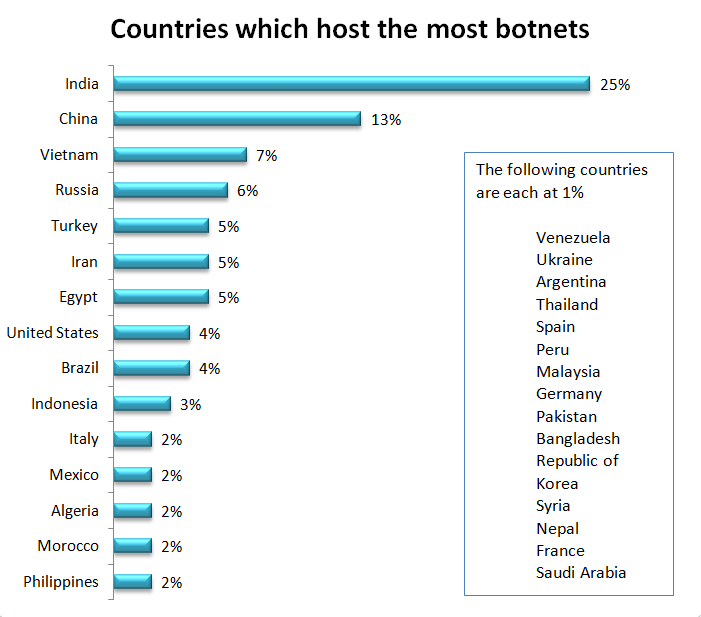
India and China hosted nearly half of the botnets. Vietnam, Russia, Turkey, Iran, and Egypt follow, with all other countries listed hosting less than 5%.
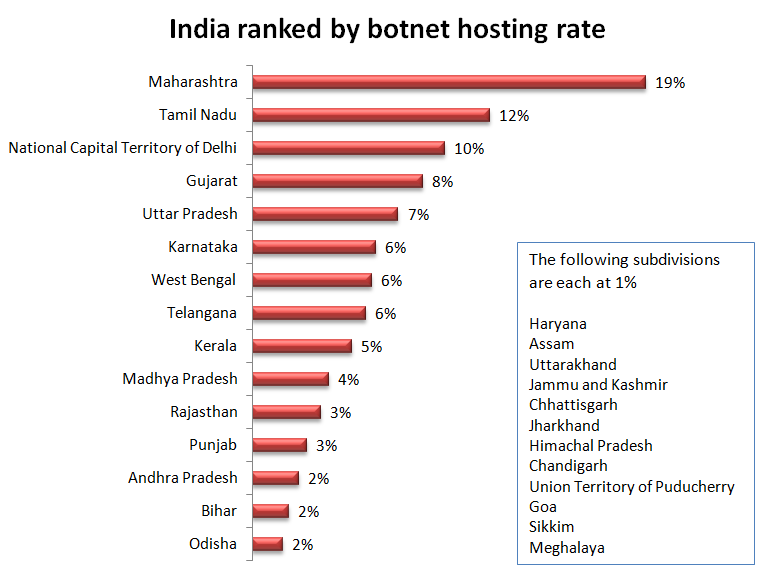
Within India, Maharashtra hosted 19% of botnets, followed by Tamil Nadu at 12%, National Capital Territory of Delhi at 10%, Gujarat 8%, and Uttar Pradesh at 7%. Twenty-two other regions each shared a small percentage of the remaining botnet hosts.
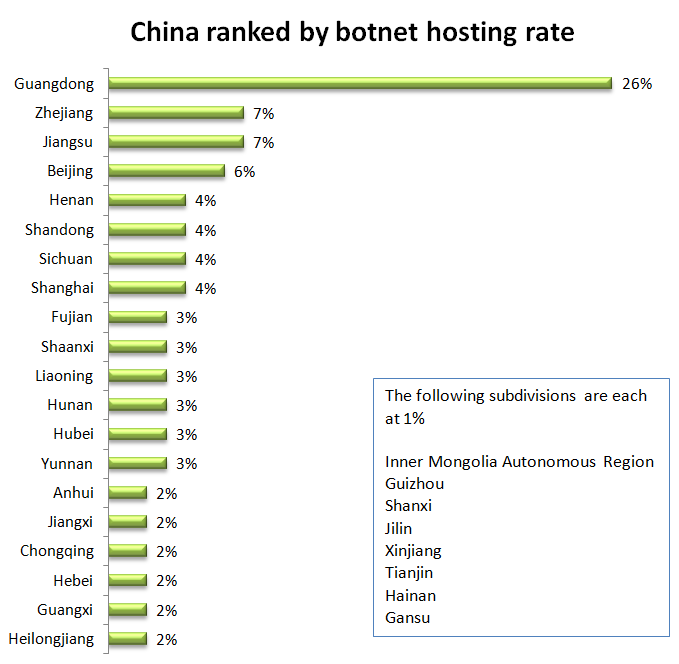
Within China, Guangdong hosted over a quarter of botnets. Zhejiang and Jiangsu each hosted 7%. Beijing hosted 6%. 24 other territories each hosted less than 5%.