IKARUSdilapidated – The New variant of Locky Ransomware
August 9, 2017, Comodo Threat Intelligence Lab unearthed a new ransomware campaign, that infects tens of thousands of victims with a simple email with an attachment and no text. According to Comodo “Beginning on Aug. 9, and lasting three days, ransomware called IKARUSdilapidated landed in tens of thousands of inboxes with an email that contains little to no content along with a malicious dropper file attachment.”
The email with the attachment carries a zip file with the name “E 2017-08-09 (xxx).xxx,” The file extension varies with each email. And as always once executed the attachment downloads, and with that ‘Welcome to the world of new ransomware called IKARUSdilapidated’.
Comodo Intelligence lab in a statement said “The attachment is an archive file, with the name ‘E 2017-08-09 (580).vbs’ where 580 is a (variable) number changing for each email and ‘vbs’ is an extension which varies as well,”. The Security Giant further said “The subjects are similar “E 2017-08-09 (580).tiff” where the extension is a document (doc), archive file (zip), pdf or image file (jpg, tiff).”
IKARUSdilapidated in the code string, Comodo researchers strongly believe that it is related to the Locky Trojan, and has a lot of matching characteristics. For example, the encrypted filenames are converted to a unique 16-letter and number combination with the .Lock file extension. “This new malware variant is read as an ‘unknown file’ and is allowed entry by organizations not using a ‘default deny’ security posture (which denies entry to all unknown files until it is verified that they are ‘good’ files and are safe to have entered the IT infrastructure).”
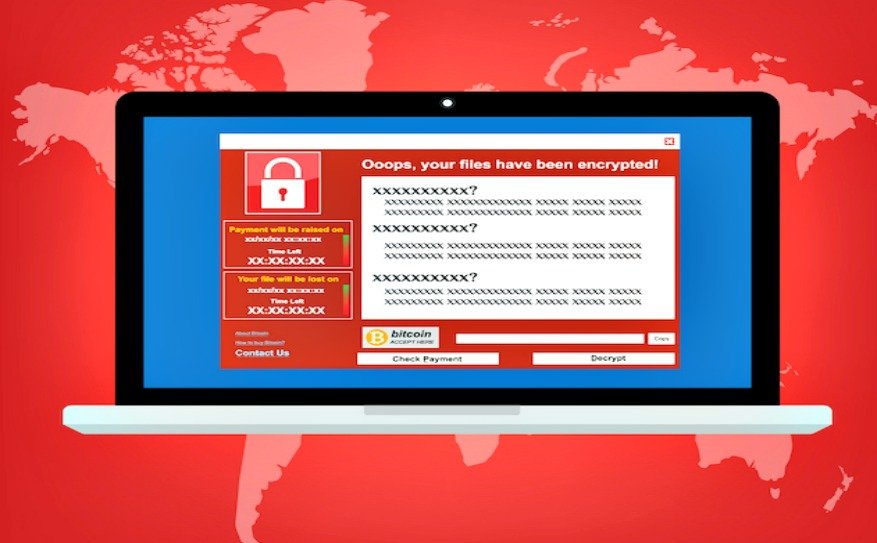
Call for Ransomware
When the attachment is downloaded and as the victim tries to open it, he gets a message that the file is unreadable, and he will have to “Enable macro’. This is the bait that is intended to trick the user to enable macros, and once it is enabled, the binary files run the downloaded encrypted Trojan. Next, the malware encrypts all the files that have a specific extension.
The victim is then asked to download the Tor browser and click the URL of a specific website, where you will be instructed to make a payment in Bitcoin.
Comodo’s endpoint protection has detected more than 60k phishing emails on August 9, 10 and 11. The company reports that from 133 countries and over 11,000 different IP were used to enable this attack. Researchers say that a particular server can be used for a specific task that one can turn this into botnets, and have a distinguished command and dedicated command and control over the server architecture.
In a yet to be published report on IKARUSdilapidated malware researchers wrote, “When the team checked the IP range owners, we see that most of them are telecom companies and ISPs. This tells us the IP addresses belong to infected, now-compromised computers,” The findings further said that Botnet is getting more sophisticated. It only makes sense to add more credence
Popularity of Ransomware
It is purely because of the fact that cyber criminals can make quick bucks. All it needs is one ignorant/novice employee to go for the kill and click on a link and open the attachment. This one click is more than enough for these criminals to make money.
“Ransomware is here to stay, and we will have to deal with it for a long time to come,” Kylie McRoberts, Google said. As Comodo says ‘It only makes sense for organizations adds more assurance to the call to follow up on the suggestion of the security experts across the world.’