Necurs Botnet’s New Scamming Spam Emails

IBM’s X-Force Cybersecurity team has published a lengthy discussion about the notorious botnet named Necurs, which is expanding its coverage for quite some time. Necurs is a spam-sending botnet, with its fleet of at least a million zombie machines, it set itself to deliver not just ransomware, but also the more covert crytomining malware for millions of unsuspecting users.
According to IBM’s X-Force, Necurs continue to get fine-tuned by its authors, as it has started a new scam email which extorts people for viewing pornographic films and marriage unfaithfulness (the scam mail accuses the receiver of doing those acts, to blackmail the users.) “Of course, this spam campaign is yet another a wide-cast net from Necurs, and the attackers have no idea whether the person they reached actually does any of these activities, but the odds appear to pay off anyway. Like other phishing and social engineering scams, it is often a numbers game,” explained IBM X-Force.
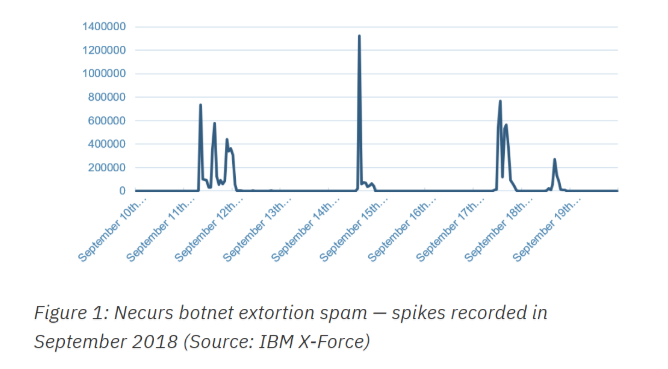
IBM has been monitoring the Necurs botnet since September 2018, with the earliest recorded activity last September 11. Unlike a typical botnet that has steady regular activity every day, Necurs chooses to only have very active actions in certain periods of time. The botnet has infected many devices from different countries in the world.
With the huge fleet of zombie computers and devices infected by Necurs, it has the capability of using 30,000+ IP addresses, which are the IP address of the infected machines themselves. IBM has revealed that Necurs was made allegedly by the same authors of other malware like Loki, Dridex, Monero miner and TrickBot, taking advantage of social engineering vulnerabilities of corporate employees and individuals.
“Email content examined by X-Force researchers revealed a number of repeating formats in which the sender falsely claimed to have malware-based control of the recipient’s email accounts and computer. The attackers went on to allege that they had infected adult sites with tracking malware and filmed the victim through his or her webcam while watching content on a supposedly compromised site. To keep the matter secret, the senders demanded that money be sent to them in bitcoin, asking for an amount between $250 to $550. If they were not paid, the attackers threatened to distribute the supposed video recording to the victim’s contact list, family, co-workers, and friends,” added IBM X-Force team.
The big innovation of the Necurs botnet-made spam is its multilanguage support. At the time of this writing, in addition to English, Arabic, French, German, Italian, Japanese and Korean languages are also supported. “Our researchers were somewhat surprised to see Arabic, Japanese and Korean on the list since those languages are harder to machine-translate and are rarely targeted by international crooks. The French email was written by someone who is likely a French speaker, and not translated online like the English version, for example. It could be indicative of some of those involved originating in Europe and possibly collaborating with counterparts in other parts of the world,” IBM X-Force said describing the language flexibility of Necurs botnet.