Explaining step by step how a penetration test, or pen-test, helps measure the security of an organization’s IT infrastructure by attempting safe exploitation of vulnerabilities. Know how a penetration test…
Read More
Many WordPress websites have come under attack via a zero-day flaw in an abandoned plugin. The “Total Donations” plugin, which was earlier used by many WordPress website owners, has now…
Read More

Late last year, we have featured here in Hackercombat.com the story about Marriot International Hotel chain data breach and the resulting accusation against China allegedly being the one behind the…
Read More
The U.S. Navy is gearing towards increasing their cybersecurity capability in order to foil any cyber attack attempts from outsiders. Dubbed as Resilient Cyber Warfare Capabilities for NAVAIR Weapon Systems…
Read More
2018 is not a good year for chip vendors, as they have not received any break when it comes to the continued stream of discoveries when it comes to their…
Read More
Email has been in use since 1971, as developed by Ray Tomlinson, the person responsible with defining the “@” symbol that separates the domain name from the user’s email name….
Read More
The results of the ‘Hack the Marine Corps’ bug bounty challenge have been announced; over 150 valid vulnerabilities have been uncovered, netting more than $151,000 in awards. It was in…
Read More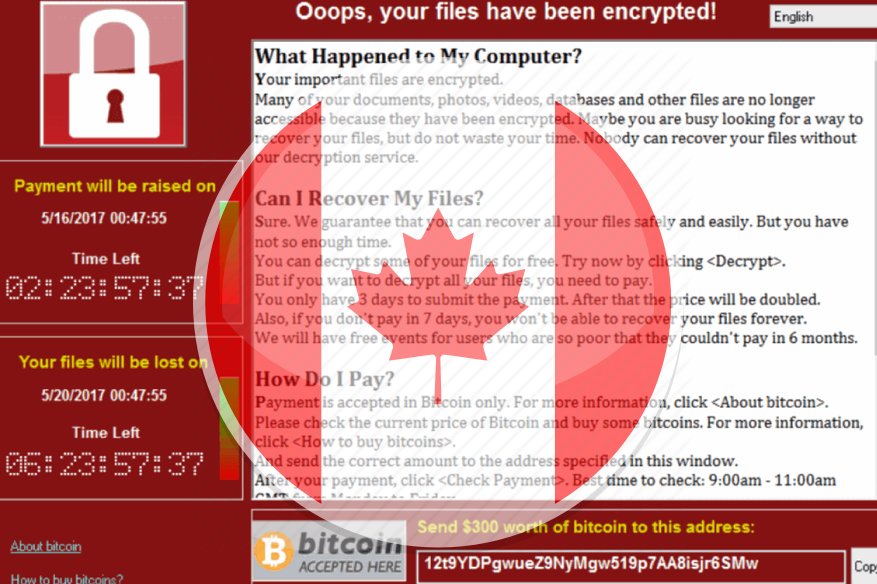
Ransomware is a very big business for cybercriminals when partnered with the victim’s inefficient or worse, non-existent backup system – that is a jackpot for ransomware authors. Ransomware attacks user’s…
Read More
As revealed by Tech Crunch, the UK-based telecommunication firm EE, endured recurrent flaws in its online system. In one week, EE fixed two security vulnerabilities that could potentially impact their…
Read More
Right after the smartphone and tablet revolution that disrupted the laptop market considerably, the next big thing is the proliferation of IoT (Internet-of-Things) devices. The days when toasters, refrigerators, home…
Read More![Penetration Testing to check for exploitable vulnerabilities [Infographic]](https://hackercombat.com/wp-content/uploads/01_infographic_Penetration_Testing.png)