What Is Application Control Systems? In today’s business environment, applications play a huge role in day-to-day business operations. With the help of applications, business processes are easier and less complicated,…
Read MoreSecurity & Privacy

Today, removable devices like flash drives and external hard drives help make data transport much easier. Large amounts of corporate data can easily be transferred from one branch office to…
Read More
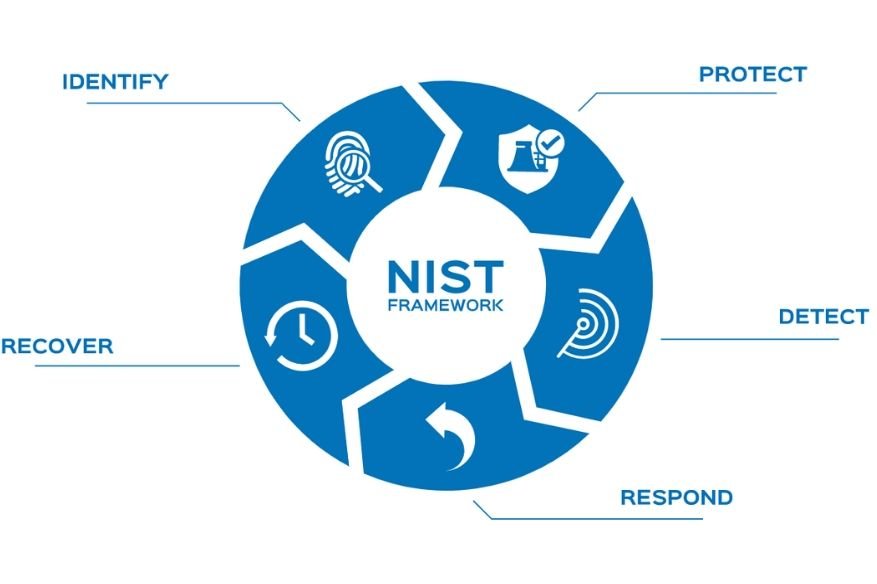
The National Institute of Standards and Framework for Cyber Security Framework (CSF) was released in February 2014 in response to the residential Executive Order 13636, which recommended a standard security…
Read More
In today’s digital world, information is the most important asset of many companies. This forms much of their business decisions and potential to earn money. This is also why others…
Read More
Dropbox is the most popular cloud storage provider in the world. Thanks to its cloud server, millions of businesses and individuals can store their files or documents in virtual memory,…
Read More
Singers, video game producers, and anyone who creates digital content all dislike one thing: piracy and copyright infringement. Since the creation of digital products, content makers have always experimented with…
Read More
Almost all mobile phones make two serious mistakes for their users: following their movements and listening to their conversations. That’s why we call it “Stalin’s dream”. Almost all phone processors…
Read More
HIPAA Definition The Health Insurance Portability and Accountability Act (HIPAA) is a bill that was signed by then-President Bill Clinton in 1996. One of this act’s main goals is to…
Read More
The types of email spams break the chain of luring offers that scare us when we check our emails. Almost everyone who has an email address sometimes has to deal…
Read More
Cybersecurity has been moving further and further towards the top of the corporate agenda for a number of years now, and for very good reason. Yet, how much do we…
Read More