Here Are 7 Critical Tips You Need To Secure Your IoT Devices

The Internet of Things (IoT) has slowly but surely taken the internet by storm, essentially turning many household objects into “smart” devices. Without a doubt, this phenomenon is following the growth of the PC industry and that of the smartphone revolution which came before. Increased use of IoT devices is now expected to quickly climb to 75 billion installations by 2025:
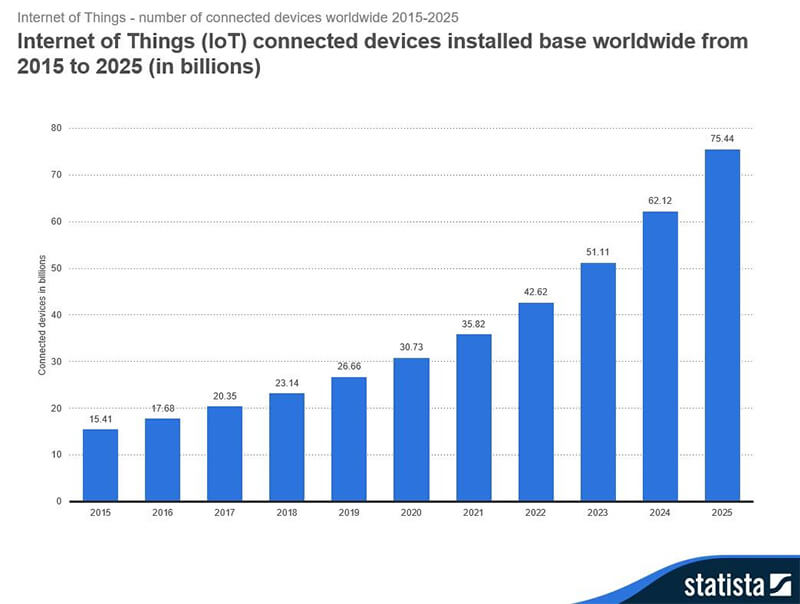
Although the IoT industry is skyrocketing, it faces some serious challenges in the area of privacy and security. Its ease of installation has created an opportunity for speedy market growth; however, the larger industry is still young and grappling to solidify its standards and how they will work to ward off cybercriminals looking to breach them at any time.
In a nutshell, IoT devices are simple, and their operating systems have usually been stripped down Linux distro like Microsoft Azure Sphere or Android Things. They are designed to be basic devices with few specific functionalities, all of which are powered by low energy-consuming hardware. This means the installation of any mainstream anti-malware software is not possible.
It is unlikely users will know if their IoT device was used in the recent cryptocurrency mining botnet or a DDOS network, but there are still certain tips to keep in mind when trying to protect IoT devices from cybersecurity problems.
1. Choose a complicated, complex password.
Like a full-blown computer and smartphone, IoT devices have a control panel page where settings can be configured. Although the page is password protected, careless users often deploy the device without changing the default admin password for IoT devices. These machines are designed to always connect to the internet, and default device passwords are widely documented online. Always ensure your default admin password has been changed to a complicated string of letters, numbers, and other characters. Choosing a simple password will make you vulnerable to dictionary and brute force attacks.
2. Prevent auto-connection.
As soon as they are removed from their packaging, IoT devices are ready to auto-connect to any open wi-fi by default. This feature was set up to ease the process of installation and deployment, regardless of the configuration of the wi-fi network. While convenient, this feature can also dangerous and compromise your trusted wi-fi network. Make sure your IoT has been configured to use just one wi-fi and not auto-connect to any nearby open and passwordless wi-fi routers.
3. Evaluate the device’s security features.
Not all IoT devices are created equal. Some manufacturers cram a few security features compared to their competition, so always check the manufacturer’s website for details on how to enable the security features built into the device.
4. Conduct research and read reviews before buying.
Aesthetics are always a nice feature in IoT devices, but these cosmetic features can sometimes come at a steep price to security. Don’t forget to read professional reviews and conduct some research on the topic before purchasing an IoT device, as the competition between vendors is stiff at the moment. There are many people marketing in the IoT world, which means customers have the advantage—vote with your wallet.
5. Update device firmware before using.
An IoT device should be allowed to auto-update its firmware before officially using it, primarily because this process fixes any bugs and security vulnerabilities in the device. After deployment, is important to check back monthly and run a security check. The longer an IoT device has been operating, the more likely it is for a manufacturer to release a fix.
6. Create a separate network or virtual LAN for IoT.
Never join the IoT device with the rest of the WLAN. Due to the simplicity of IoT, they are always a target of cybercriminals. Use an isolated separate router or create a virtual LAN in the network switch for the IoT devices. This enables a solid layer of security which works in IoT devices to the PC, smartphone, and tablet.
7. Don’t hesitate to throw away an IoT device if it has a bug or serious vulnerability. If a model of a certain device is abandoned by its manufacturer, you may want to consider discarding it and using a more modern, supported model. The use of a non-supported model is like using a Windows XP PC today—the OS is no longer patched and can pose online risks.