Hacking is a common thing today. Almost everyone talks of hackers and hacking, though most people don’t have an idea of the different kinds of hacking techniques that are there….
Read More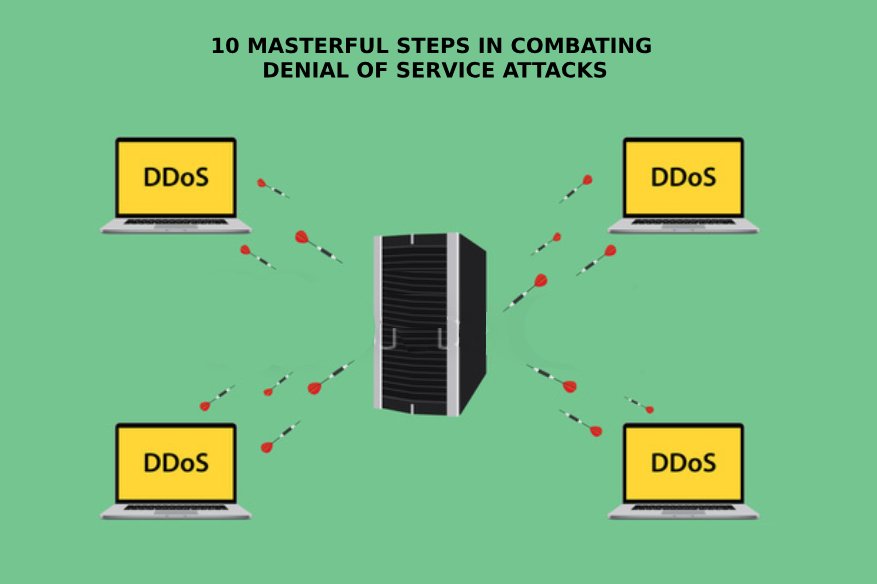
We could define DDoS (Distributed Denial of Service) attacks as the exclusive appropriation of a resource or service with the intention of avoiding any third party access. Also included in…
Read More

In this age of post-Snowden era, a typical user is somewhat aware that spying for personally identifiable information is a lucrative business for both cybercriminal organizations and state-actors connected with…
Read More
People use VPNs to browse the internet safely. It is a great way of protecting your privacy, encrypting the data, and hiding your geolocation. There are paid VPN services, but…
Read More
Cost cutting is a critical issue with many firms nowadays, as everyone wants to maximize profits while not increasing spending. One such spending habits that companies have started to cut…
Read More
Mcafee a few weeks ago has made a shocking expose about Remote Desktop user accounts being sold online at cheap prices, more particularly in the Dark Web. RDP is a…
Read More
TorrentFunk has been there for years, providing every movie lover the best of their requirement. The website gives you everything software, TV shows, movies, and games etc. All that the user does…
Read More
Tech giant Apple has updated its App Store privacy guidelines. The company now restricts app developers to collect and harvest data from the devices they were installed to. One of…
Read More
Let’s do away with the usual introduction about hacking. Today almost anyone who uses the internet is familiar with the word ‘hacking’ and knows that in today’s scenario, anyone could…
Read More