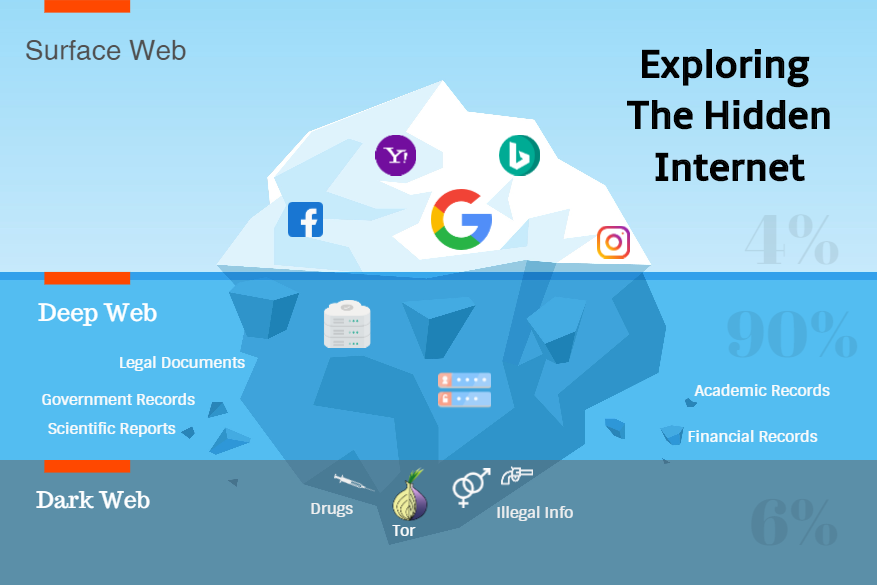
When we have to search for something on the Internet, our mind, by default, goes to Google or Bing. Our mind is tuned, and we get the results we seek….
Read MoreSecurity News

All know that downloading movies and software from the torrent network could infect your computer with malware, but what is more heartbreaking is when you see a popular, and trusted…
Read More
Most small businesses just rely on an antivirus tool to mitigate cyber risks, despite the fact that hackers show an increasing tendency to target small businesses. Small businesses leave many…
Read More
Currently, most computers are connected to the network, and various information is exchanged beyond national borders. Mobile devices such as smartphones and tablets have also been used in business, personal…
Read More
Phishers are in a huge advantage these days with the growth of social media platforms such as Facebook, Twitter, Instagram, and even Youtube. People can and continue to navigate away…
Read More
A fatal cross-site request forgery (CSRF) vulnerability on Facebook was discovered by a security researcher, and interestingly it allowed hackers to take over Facebook accounts with a simple one-click on…
Read More
The Content Management System market is very competitive these days, with a partial list of all CMS softwares that exist can be seen in a Wikipedia page. Whether the web…
Read More
What is a Secure Web Gateway (SWG)? For the perspective of a typical Joe or Jill of today’s computing, Secure Web Gateway is an alien name. However, it is simply…
Read More
The Dark Web is once again is hosting a ‘clearance sale’ of at least 617 million user credentials, collectively coming from recently hacked services including ShareThis, Whitepages, 500px, Dubsmash, and…
Read More