Today's Featured

Protect Your Devices With Free Virus Removal
Computer viruses are extremely hazardous, which is why it’s crucial to secure your devices with reliable malware removal programs. These free applications serve as your second line of defense against…
Read More
Implementing Zero Trust
Zero trust is an adaptable security framework designed to address today’s cyber security challenges. It employs microsegmentation and data-centric policies, verifying users, devices, applications irrespective of network location as well…
Read More
CDK Cyber Attack
This attack had all the hallmarks of ransomware attack and targeted CDK Global systems used by auto dealerships to manage sales, finance and service operations. Due to outdated technology, ineffective…
Read More

5 Ways to Mitigate Risk in Cybersecurity
Cybersecurity refers to practices designed to defend computers, mobile devices, electronic data storage platforms and networks against attacks such as ransomware extortion and data breaches. Preventative techniques are key in…
Read More
What is Malware
Malware refers to any form of malicious software which aims to disrupt, harm or steal private information for criminal use. Furthermore, malware can mine cryptocurrency for cybercriminals as an additional…
Read More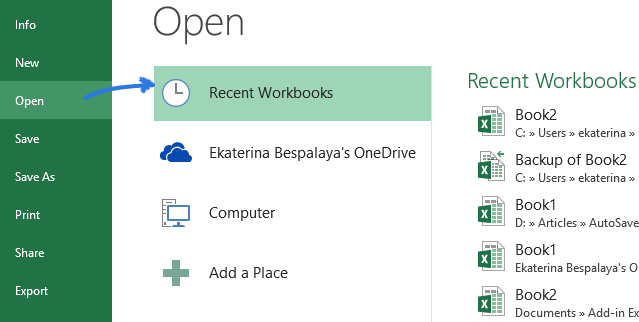
How to Recover an Unsaved Excel File
If your Excel file was left unsaved by accident, don’t fret – Microsoft understands mistakes happen and provides built-in functionality to help recover it. To recover an unsaved file, navigate…
Read More
How to See Who Blocked You on Facebook
If you suspect someone has blocked you on Facebook, various methods exist to investigate their actions. One option would be searching for their name; they may have blocked you if…
Read More
How To Access Your Photos On iCloud
iCloud can be an easy and secure way to back up photos and videos, but accessing those files across devices may prove challenging. Thank goodness there are multiple ways to…
Read More
Why is the iPhone Force Restart Not Working?
If the iPhone force restart does not work as intended, there may be an issue with the iOS system. To address this, look for physical damage to buttons used for…
Read More
YouTube Not Working on iPhone? Here’s How to Fix It
If the YouTube app on your iPhone is crashing or will not open, there are various fixes you can try, such as force quitting the app, rebooting your device, and…
Read More






