Have you ever experienced being hacked in your Android smartphones and tablets? How do you feel? If you have already experienced hacking, well, you are not alone. Today, there are…
Read MoreSecurity News

The official website of the US effort President Donald Trump revealed data, according to security experts, that may have allowed hackers to intercept emails and to send emails on behalf…
Read More
If the FBI finds that foreign hackers have compromised the electoral district networks, you may not be aware of that until after the election is over. The governor and other…
Read More
If you want to boost usability, increase conversions, improve bounce rates, and rank higher on search engines, you must consider site speed. However, before we go any further, you must…
Read More
Global shipping and e-commerce firm Pitney Bowes announced on Thursday that a piece of malware known as Ryuk has triggered the latest network disruptions. On Monday, the company told customers…
Read More
If you own a jailbreak-free iPad, you have the assurance that your device is virus-free. Moreover, you’re safe from any vital issues caused by malware because it doesn’t target iPads…
Read More
We all know of the exponential growth of cybercrimes. The question now is, how do we stay ahead of a possible data breach? Some experts in the commercial real estate…
Read More
A citizen of Singapore was arrested in the United States for a large-scale mining operation using robbed identity and credit card data. The 14-count indictment notes that between October 2017…
Read More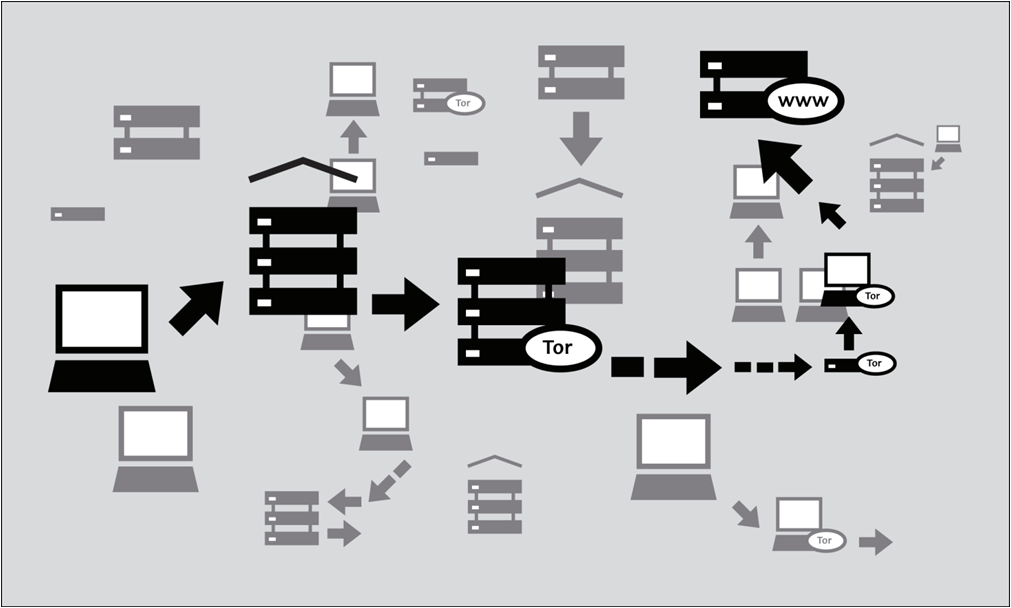
If you’re one of those who do a lot of things online using a mobile device, you should be concerned about Internet security. The virtual private network (VPN) is a…
Read More
The’ net’ in’ internet’ is a network. It’s also technically an internet network— a computer network. Are you still confused? We refer to these independent computer networks as autonomous systems…
Read More
