Julian Assange’s lawyers want to see if hacking is protected by the First Amendment. London’s Metropolitan Police arrested Assange on Thursday at the Ecuadorian Embassy, where he’d been granted asylum…
Read MoreTech

Here are the IT Security acronyms that you will like to know what it stands for in technology world. IT Security A measure that help organizations to verify that their…
Read More
A security technology that is built on or linked into an application runtime environment, and is capable of controlling application execution, and detecting and preventing real-time attacks,” This is how…
Read More
Both American Express and Netflix enjoy a lion share of their respective customer base, they offer their customers a convenient way to shop and watch whatever movie they wish respectively….
Read More
What is a Secure Web Gateway (SWG)? Web filtering is used by Secure Web Gateway (SWG) solutions to enforce enterprise Internet access regulations. They also block unwanted software, particularly malware,…
Read MoreAre you ready to put Artificial Intelligence (AI) to work, as it gives organizations unparalleled access to cutting-edge technology. The widespread adoption and growing demand is expected to grow by…
Read More
With around 2 million+ apps in the Apple App Store, it is highly difficult to find hidden gems. Here in Hackercombat.com, it is also our interest for you to learn…
Read More
Cloud technology and cloud security are key to the growth of any modern business. Businesses today need a safe and secure way to store and access their data. It’s not…
Read More
Tutu App: What’s it? The Tutu App, which lets you download and install premium games and apps for free, has become immensely popular in Android and iOS. At the same…
Read More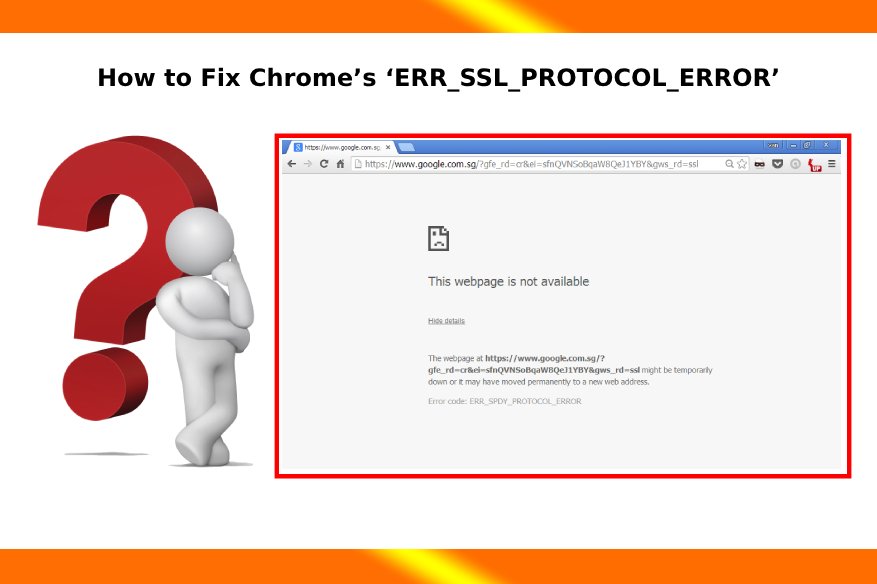
err_ssl_protocol_error’ – If you use Google Chrome to access the internet, you’ve probably seen the error “This site can’t provide a secure connection” or the ERR SSL PROTOCOL ERROR notice…
Read More

![Adopting Artificial Intelligence in Your Business [Infographic]](https://hackercombat.com/wp-content/uploads/Adopting-Artificial-Intelligence-in-Your-Business-Infographic.jpg)