iOS Version of Exodus Android Spyware Doing the Rounds
Security researchers have discovered a dangerous iOS spyware strain that was seen earlier this year on the official Google Play Store. Exodus is the name of the spyware and it…
Read More
Security researchers have discovered a dangerous iOS spyware strain that was seen earlier this year on the official Google Play Store. Exodus is the name of the spyware and it…
Read More
It’s time to welcome the Google Duplex Assistant, which will soon be available on all iPhones and most Android phones as well… It was at Google’s I/O developer conference in…
Read More
The European Union has flexed its muscles again to combat anti-competitive behavior. This time around, it is Google that is in the receiving end of the order. The search giant…
Read More
Antimalware Apps Recently, Google went out of their way to clean-up Google Play Store from apps pretending to be antimalware apps, but really just consuming resources of the Android device….
Read More
Right after Windows, antimalware vendors have set their sights on Android as their next “platform” to protect (or at the very least claiming to protect). As Windows is an undisputed…
Read More
Google has been slapped by a 50-million Euro fine by CNIL (Commission Nationale de L’informatique et des Libertés), France’s Data Regulation Agency due to GDPR (General Data Protection Regulation) violation….
Read More
2018 can be summarized as the year when strict implementation of customer data protection policies was felt by the public, regardless of where they are located in the world. This…
Read More
Canada has apparently imitated European Union’s GDPR, that is the latest news from the country’s Office of Privacy Commissioner of Canada (OPC). Under the new policy, starting November 2018, all…
Read More
The fallout against Facebook has started, caused by the user data exposure breach due to its Cambridge-Analytica fiasco, starting with the UK’s ICO (Information Commissioner’s Office). ICO has slapped the…
Read More
Denial-of-service (DoS) attacks are the antecedent to DDoS attacks. Earlier, DoS attacks were the main source of disrupting computer systems on a network. It originates from a single machine and…
Read More
Facebook, which has suffered the biggest ever outage in its history, is struggling to deal with it. The partial outage that affected some users of Facebook and other platforms owned…
Read More
When Did UPnP and SSDP Became Mainstream? Universal Plug and Play (UPnP) was considered revolutionary when it was introduced to Windows Millennium Edition nineteen years ago, in 2000. It was…
Read More
Six years jail time, that may become the penalty awaiting the 6 young hackers, two who were allegedly responsible for DDoS (Distributed Denial of Service) attack against Ukraine government and…
Read More
We could define DDoS (Distributed Denial of Service) attacks as the exclusive appropriation of a resource or service with the intention of avoiding any third party access. Also included in…
Read More
Basic tips that could help you clean your WordPress website if it gets malware-infected. This includes scanning the website, checking backup files, changing passwords, re-installing WordPress, re-installing themes and plugins,…
Read More
Understanding how to choose a firewall, the network security system that monitors and controls all incoming and outgoing traffic based on a set of rules. Learn how to choose the…
Read More
Explaining step by step how a penetration test, or pen-test, helps measure the security of an organization’s IT infrastructure by attempting safe exploitation of vulnerabilities. Know how a penetration test…
Read More
How to find out if your WordPress website is hacked? Know all about the different signs which indicate that your WordPress website might be hacked. Check for signs like invalid…
Read More
Computer viruses are extremely hazardous, which is why it’s crucial to secure your devices with reliable malware removal programs. These free applications serve as your second line of defense against…
Read More
Zero trust is an adaptable security framework designed to address today’s cyber security challenges. It employs microsegmentation and data-centric policies, verifying users, devices, applications irrespective of network location as well…
Read More
This attack had all the hallmarks of ransomware attack and targeted CDK Global systems used by auto dealerships to manage sales, finance and service operations. Due to outdated technology, ineffective…
Read More

Cybersecurity refers to practices designed to defend computers, mobile devices, electronic data storage platforms and networks against attacks such as ransomware extortion and data breaches. Preventative techniques are key in…
Read More
Malware refers to any form of malicious software which aims to disrupt, harm or steal private information for criminal use. Furthermore, malware can mine cryptocurrency for cybercriminals as an additional…
Read More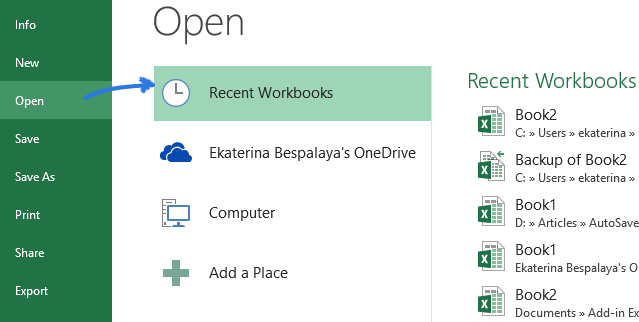
If your Excel file was left unsaved by accident, don’t fret – Microsoft understands mistakes happen and provides built-in functionality to help recover it. To recover an unsaved file, navigate…
Read More
If you suspect someone has blocked you on Facebook, various methods exist to investigate their actions. One option would be searching for their name; they may have blocked you if…
Read More
iCloud can be an easy and secure way to back up photos and videos, but accessing those files across devices may prove challenging. Thank goodness there are multiple ways to…
Read More
If the iPhone force restart does not work as intended, there may be an issue with the iOS system. To address this, look for physical damage to buttons used for…
Read More
If the YouTube app on your iPhone is crashing or will not open, there are various fixes you can try, such as force quitting the app, rebooting your device, and…
Read More